What is 0xxx Ransomware? Detection, Protection, and Recovery
0xxx is a type of ransomware that first surfaced in early 2021 and has been causing massive damage to organizations around the world ever since. Basically, 0xxx is ransomware infection that encrypts files on a user’s PC by adding .0XXX to common file extensions such as .txt, .docx, .xlsx. Once infected, the renamed files are no longer accessible by users. To regain access to the locked data, the victim is asked to pay a ransom in bitcoin. Then the cybercriminals behind the 0xxx infection claim that they will provide a decryption tool in return.
After a short introduction about ransomware and its two main types, this blog post covers the 0xxx ransomware, data protection methods and how to recover data if your system is infected.
What is Ransomware?
Ransomware is a type of malware that usually installs itself on a device without the knowledge or consent of the user. In most cases, once a device is infected, ransomware encrypts some or all files, and cybercriminals demand payment in return for a decryption tool (that may or may not be provided even after a ransom is paid). Ransomware is most often installed by clicking on links in phishing emails or opening malicious attachments from unknown senders.
Not only does ransomware block access to files but it can also spread from one device to another within a network by copying itself into network storage devices or cloud-based storage accounts. This alone classifies ransomware as one of the more dangerous forms of malware and cyber threats in general.
The idea behind ransomware is to make it as difficult as possible for victims to retrieve their data. Some ransomware variants sacrifice data integrity after encryption or even allow hackers to make changes or delete files. This makes it exceptionally more difficult for victims to recover data and may result in permanent loss of data without backups to use for point-in-time restores.
Types of ransomware
Ransomware can be classified into two main types: non-encrypting and encrypting.
Non-encrypting ransomware does not encrypt files. Instead it holds your system hostage. This type of ransomware displays a message during operating system startup or when opening a browser, stating that the device in use has been taken over by the government (or a government agency) due to illegal activities. A ransom is demanded in exchange for dropping the alleged charges against you and unlocking your device. Generally, non-encrypting ransomware does not affect your data integrity and can be removed from a device.
On the other hand, encrypting ransomware infiltrates your device, typically via a malicious email attachment or a phishing link and blocks access to files and programs on that device until you pay the specified ransom. But even after paying the ransom, you are not guaranteed to receive a decryption tool to regain access to your files. In some cases, attackers may also threaten to make public some sensitive data.
Encrypting ransomware is the most harmful type of ransomware and arguably one of the most vicious cyber threats to have appeared in recent years. Companies that pay large amounts of money to get their data back encourage cybercriminals to expand their activities and target more victims.
What is 0xxx?
0xxx is a type of encrypting ransomware that uses the AES and RSA algorithms to encrypt files. AES and RSA are powerful encryption security standards employed by governments and organizations with sensitive data. Throughout the years, the AES and RSA standards have slowly become a staple of the ransomware world, as both algorithms are considered the main driving force behind some of the most notorious strains, like Cryptolocker and Teslacrypt.
Just like other ransomware in the same category, such as Redeemer, Ouelezin Zebi and Iqll, 0xxx denies access to files by encrypting them, renames their extensions, and creates a text file in every single folder on the infected drive containing a message demanding a ransom.
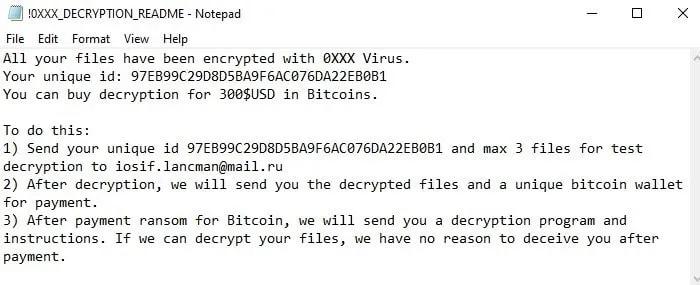
The generated “!0XXX_DECRYPTION_README.TXT” file includes a set of instructions that victims must follow to decrypt their data. But first, victims are informed that all their files have been encrypted with the 0xxx virus and that a decryption tool may be bought in bitcoin.
The victims are then asked to email the unique ID (a 32-digit uppercase hex code) assigned to them along with three encrypted files to the provided address. As a proof of concept, the victims are emailed back with the three previously sent files, completely decrypted and virus-free. In the same email, victims will receive the bitcoin wallet address into which the specified ransom must be transferred. Finally, the cybercriminals behind the 0xxx virus pledge to send the decryption tool once payment is made.
Here is a screenshot of an 0xxx ransomware text file instructing a victim on how to pay the ransom:
How does 0xxx infect computers?
While ransomware relies on a multitude of infection vectors to propagate, the two most common ways used by cybercriminals nowadays to spread 0xxx are phishing emails and Trojan malware.
The most prevalent of all vectors, phishing has become more sophisticated and dangerous than ever before. A phishing email is a scam email that tricks the recipient into clicking on a link or downloading malicious content that can lead to a ransomware attack. Phishing emails are designed to look like they are sent from a trusted source, for example, a bank or a credit card company. Such emails can include files that act as ransomware carriers. Once downloaded and installed, the malicious files can immediately infect the system with the 0xxx ransomware.
A Trojan is a type of malware that, on the surface, appears to be a legitimate piece of software but is programmed to cause damage to data on a system or network. Trojans are often accidentally downloaded from suspicious websites claiming to host illegal activation tools (also referred to as “crack”) and fake updates for applications like Google Chrome or Microsoft Office. When installed, Trojan malware can open a backdoor to a malicious actor, who can then view and manipulate data on the host system. If the perpetrator successfully gains full access to the system, then injecting ransomware, like 0xxx, can be easily achieved.
How to Detect 0xxx Ransomware?
There are a few indicators that can help you detect 0xxx ransomware on your device:
- Suspicious changes to filename extensions: The 0xxx ransomware’s first order of action is to add .0XXX to all file extensions. This particular ransomware keeps the original file names intact. For example, document.pdf becomes document.pdf.0XXX. This is not a simple filename extension rename but rather an indication that the file has been encrypted.
- High CPU activity: The 0xxx ransomware consumes a lot of resources, and, as a result, programs can be noticeably slower to run and load. Encrypting and renaming thousands of files is a CPU-intensive task and can slow down your system to the point of unresponsiveness.
- Inability to access files: The 0xxx ransomware’s primary goal is to deny you access to files. When encrypted, files and documents can’t be opened and require a decryption tool to be restored to their original state. The decryption tool can only be provided when the specified ransom has been paid.
- Abnormal network communication: If your system is infected by 0xxx ransomware, you may experience internet slowdown. Cyber criminals behind ransomware attacks can establish a communication system between their servers and infected computers to manipulate files. This may lead to constant connection problems.
How to Protect Systems Against Ransomware?
Organizations of all sizes must not underestimate the threat of ransomware. No matter how robust your security system is, ransomware can still find its way onto your or an employee’s computer. No organization is fully immune to the threat of ransomware. Therefore, to protect your organization’s data against any form of ransomware, you have to adopt a layered approach.
Educate coworkers
Create an effective employee training program on ransomware to educate coworkers about what ransomware is and how it works. You should also cover how to avoid getting infected by malware and how to respond to a ransomware attack if and when it does happen.
Regularly emailing employees about ransomware news and the dangers associated with cyber threats is a good practice, especially if your organization’s workflow relies on cloud-based productivity and collaboration tools like Microsoft Office 365.
Conducting regular ransomware awareness training sessions can greatly help employees to differentiate between fraudulent and legitimate content found in emails, attachments and websites. Consequently, the probability of erroneous actions such as opening phishing links and downloading malicious software can significantly decrease.
Configure email filters
Most major email services include filters that can protect you or your coworkers from cyber threats, including ransomware. Some services offer advanced security measures like automatically detecting and rejecting suspicious emails from untrusted or unknown sources. I previously covered how to configure Microsoft Defender for Office 365 anti-phishing and anti-impersonation policies and listed all the steps required to maximize email security.
Scan and monitor your system
Running scheduled full system scans via an updated antivirus or anti-malware program can help detect suspicious activity such as a mass file extension rename or unusual disk usage. An antivirus with the latest definition can neutralize a ransomware threat by quarantining the downloaded malware software, thus limiting the spread of the infection across your system and network. Also, make sure to install the most current security patches for your operating system as soon as they become available.
Data backup
Regularly running backups following the 3-2-1 backup rule ensures that your data can survive a ransomware attack with minimal damage. The 3-2-1 rule is a commonly used and effective method for backing up data. The rule dictates that you should keep at least 3 copies of your data and store them on 2 different kinds of media while keeping 1 of the copies offsite.
Also, you may want to adopt new backup technologies, like immutable backups, to protect your data assets from ransomware. With immutable backups, which rely on the WORM (Write Once Read Many) model, your data is backed up to a storage volume that can be written once. The data on that volume can be accessed many times but cannot be overwritten, changed or deleted for a specified time period.
How to Recover Files after a 0xxx Ransomware Attack?
If your computer is infected with 0xxx ransomware, you can not recover any data unless you pay the ransom, or at least that’s what the cybercriminals want you to believe. While antivirus or anti-malware software can remove the malware and limit its spread, they do not provide you with the option of restoring already infected files. The only solution is to recover the files from a backup, if one was created before the infection and stored in a different location.
If you’re looking for a complete data protection solution, consider deploying NAKIVO Backup & Replication. NAKIVO Backup & Replication can ensure high-end protection for all environments, including virtual, physical, cloud and SaaS. Use the solution to protect VMware vSphere, Microsoft Hyper-V, Nutanix AHV, Amazon EC2, Windows/Linux machines and Microsoft 365 data.
NAKIVO Backup & Replication offers your backed-up data another layer of ransomware protection. The solution allows you to make your backup data immutable for as long as you need both in local Linux OS storage or in Amazon S3 buckets. This way, your backup copies cannot be modified, overwritten or deleted until that period expires. With your backups locked, backup data is protected from encryption by ransomware and you can quickly recover it if a malicious attack like 0XXX hits your systems.