What Is Immutable Data Storage for Backups?
Data backups can help recover data if a main production copy is corrupted or deleted. However, with the high risk of cyberattacks and other threats, backups are also vulnerable.
One of the best ways to protect backup data against any modifications or deletions is by using storage that supports immutability. Learn about data immutability, how immutable storage works, and why immutable data storage improves the chances of data protection and recovery.
What Is Data Immutability?
Data immutability is a concept in computer science and data management that refers to data that cannot be changed after it has been created. In an immutable data model, once data is created, it cannot be modified or updated; instead, any changes result in the creation of new data, leaving the original data unchanged (if the changes can be applied). This approach has important implications and benefits.
Immutable data is not always the best choice, as there are scenarios where mutable data is more efficient or appropriate. However, in many cases, especially in backup systems, concurrent or distributed systems, immutability can simplify development and improve reliability.
What Is Immutable Storage?
Immutable storage is a type of data storage where once data is written or stored, it cannot be modified, altered or deleted for a specified period of time, if at all. This concept is often used in the context of data preservation, data protection, data compliance and data security. Immutable storage systems are designed to ensure the integrity and immutability of data, typically for legal or regulatory reasons or to protect critical information from unauthorized changes or deletion.
Immutable storage adds an extra layer of data security. Once data is written to an immutable storage system, it becomes resistant to unauthorized modifications, protecting it from cyberattacks and insider threats. Immutable storage can be used in scenarios where maintaining a secure and unbroken chain of custody is crucial, such as evidence storage in legal cases or storing financial transaction records. An example can be video surveillance footage that is written once and cannot be tampered with or deleted to be used as proof when investigating legal activities.
Immutable storage systems are deployed to retain data for a specific period, ensuring that it remains unchanged and accessible for auditing, compliance, or archiving purposes. This is crucial in industries such as finance, healthcare, and legal, which are fields with stringent data retention requirements. Whether for data protection, regulatory compliance (for example, GDPR), or enhanced security, immutable storage is a critical component in ensuring data integrity and resilience against tampering or unauthorized changes.
How Does Immutable Storage Work?
Immutable storage works by implementing mechanisms and policies that prevent data from being modified, altered, or deleted after it has been written or stored. The specific methods for achieving immutability can vary depending on the technology and architecture of the storage system. Techniques and principles used in immutable storage are:
- Write-Once-Read-Many (WORM). WORM storage is designed to allow data to be written only once and once written, it cannot be changed or overwritten. This is often achieved using physical or logical mechanisms that lock data after it’s been written, preventing any further modifications.
- Data versioning. Some immutable storage systems support data versioning, where each modification to the data results in a new version. Older versions of the data are preserved, allowing you to access historical versions while ensuring that the original data remains unchanged.
- Locking and access controls. Immutable storage systems often incorporate access controls and permissions to prevent unauthorized users from attempting to modify or delete data. Only authorized individuals or processes can write to the storage, while others can only read data.
- Retention policies. Immutable storage systems typically include retention policies that specify how long data must be preserved in an unaltered state. This allows you to set immutability for a specific time. Once this retention period expires, data may be eligible for deletion.
- Cryptographic hashing. Many immutable storage systems use cryptographic hashing techniques to ensure data integrity. When data is written, a hash value (a fixed-length string derived from the data’s contents) is computed and stored alongside the data. Any attempt to modify the data will result in a different hash value, indicating tampering.
- Content-addressable storage. This is a storage architecture that assigns a unique identifier (typically a cryptographic hash) to each piece of data. This identifier is used to retrieve data rather than traditional file paths. Once data is written, it cannot be modified without changing its identifier.
- Audit trails. To ensure compliance and track any access or modification attempts, immutable storage systems often maintain detailed audit logs that record all interactions with the stored data.
- Hardware and software safeguards. Immutable storage may utilize hardware or software safeguards to protect data from physical and logical threats, such as tamper-evident seals, secure hardware modules, or distributed consensus algorithms.
Immutable storage is often used in combination with other technologies like blockchain, digital signatures and secure timestamps to further enhance data authenticity and security. The specific implementation of immutable storage can vary widely based on the needs and requirements of the organization or industry it serves.
Air Gap vs Immutable Storage
An air gap is a security measure used in computing and data management to physically and logically isolate a system or network from unsecured or potentially compromised environments. The term “air gap” implies that there is a literal gap or physical disconnect between the protected system/data and external networks, making it difficult for data to be accessed, altered, or compromised by unauthorized users or cyberattacks.
Air-gapped storage is a storage media that is physically disconnected from a computer or network. Air gaps are commonly used for highly sensitive or critical systems, such as those handling classified information, critical infrastructure control systems, and secure government or military networks.
An air gap provides a strong layer of security by isolating a system or data from external networks, but it does not inherently make storage immutable. Air gapping primarily focuses on isolating a system or network from external threats but does not guarantee data immutability on its own. Organizations can combine air-gapped environments with additional security measures and data immutability practices and policies to achieve cyber resilience within that isolated context to protect data from unauthorized changes.
An example of air-gapped storage
SAS, SATA, or USB HDD disconnected from a server or storage array is a common example of air-gapped storage. Files stored on such a hard disk drive (HDD) cannot be modified because this device is physically disconnected and powered off. It is inaccessible for software. Data stored on this disconnected hard disk drive is protected against ransomware attacks and other unwanted changes.
However, this protection is not achieved by using immutable technologies as in the case of modern immutable storage. There are no hardware write-protecting switches and there is no software that ensures write-protection for a standard hard disk that is in a powered-off state. That’s why air-gapped storage and immutable storage are different, despite the fact they are used for similar purposes.
Tape cartridges are also considered air-gapped storage. After writing a backup to tape, the ejected tape cartridge cannot be accessed by ransomware and the backup data cannot be modified.
Air-gapped storage requires more effort and time for management compared to immutable storage that can be implemented on a server, in a local or public cloud.
Immutable Cloud Storage Solutions
Immutable cloud storage solutions refer to cloud-based data storage services or systems that offer immutability as a core feature. These solutions ensure that once data is stored in the cloud, it cannot be modified, altered, or deleted for a specified period or according to specific policies and the principles of immutable storage. Immutable cloud storage is particularly valuable for organizations seeking to protect data integrity, meet compliance requirements, enhance data security, and implement data retention strategies in the cloud environment.
Examples of immutable cloud storage
Immutable cloud storage solutions are offered by various cloud service providers and they are designed to provide data immutability and protection against unauthorized modifications or deletions. Several cloud service providers offer immutable cloud storage solutions as part of their portfolio. For example, Amazon S3 (Simple Storage Service) offers Object Lock, a feature that enables data immutability for S3 objects (immutable object storage). Microsoft Azure offers Azure Immutable Blob Storage, which allows organizations to create and manage immutable data in Azure Blob Storage. Let’s overview examples of immutable cloud storage solutions from some major cloud providers:
- Amazon S3 Object Lock. Amazon S3 offers a feature called Object Lock that allows users to create immutable objects within their S3 buckets to provide immutable object storage in the public cloud. Users can choose between two modes: Governance mode, where administrators can set retention policies, and Compliance mode, where once an object is locked, it cannot be deleted or modified until the retention period expires.
- Microsoft Azure Immutable Blob Storage. Microsoft Azure provides Immutable Blob Storage as part of its Azure Blob Storage service. Immutable Blob Storage allows users to set retention policies on their blob containers, preventing any modification or deletion of blobs until the retention period has elapsed.
- Google Cloud Storage Object Versioning. Google Cloud Storage offers object versioning as a way to achieve immutability. When versioning is enabled, every modification to an object creates a new version of that object, preserving the original. Users can configure object lifecycle policies to manage versions over time, which can include setting retention periods for immutability.
- IBM Cloud Object Lock. IBM Cloud Object Storage provides Object Lock, a feature that allows users to enforce immutability for specific objects within their buckets. Similar to other cloud providers, Object Lock provides both Governance and Compliance modes for different levels of control over data retention and immutability.
- Oracle Cloud Storage Service Object Lock. Oracle Cloud Storage Service offers Object Lock, which allows users to create immutable objects with customizable retention periods. This feature is useful for organizations subject to data retention regulations or those requiring strict data preservation.
These examples highlight how various cloud providers offer solutions to ensure data immutability, primarily through the creation of immutable objects or the use of versioning and retention policies.
Local Immutable Storage
Local immutable storage refers to data storage that is physically located on a device or system and is designed to ensure the immutability of the stored data. Unlike cloud-based immutable storage solutions, which rely on remote servers and services, local immutable storage operates within the confines of a single device, server, or on-premises infrastructure. This type of storage is particularly useful for scenarios where data needs to be protected from unauthorized modifications or deletions on the local level.
The key characteristics of local immutable storage are:
- Hardware-based write protection. Local immutable storage can be achieved through hardware mechanisms that physically prevent data from being overwritten or modified. For example, write-protected storage devices or media, such as optical discs, allow data to be written once and then protect it from subsequent changes.
- Filesystem features. Some filesystems support features that can be used to implement local immutability. For instance, in Linux-like operating systems, you can use the
chattrcommand to set attributes like “i” (immutable) on files, preventing them from being modified or deleted. - Specialized software. There are software solutions designed to create local immutable storage environments. These often rely on cryptographic hashing, digital signatures, and access controls to ensure data integrity and immutability.
Examples of Local Immutable Storage
The examples of local immutable storage used in practice are:
- Optical discs (CD-R, DVD-R, Blu-ray disc): Write-once optical discs are a classic example of local immutable storage. Once data is burned onto these discs, it cannot be altered or deleted without physically damaging the medium.
- Write-protected storage devices: SD flash cards come with write-protect switches and some USB hard drives have mechanisms that prevent data from being modified once the write protection is enabled.
- Immutable filesystems: Some specialized filesystems, like WORM (Write-Once-Read-Many) filesystems, are designed to enforce data immutability at the filesystem level (for example, Sun QFS). They prevent changes to stored data after it has been written.
- Blockchain databases: Blockchain databases are a form of local immutable storage used for decentralized applications. In blockchain, data is stored in a series of blocks, with each block containing a cryptographic hash of the previous one. This chain of blocks ensures the immutability of stored data.
- Secure Hardware Modules: Some hardware security modules (HSMs) and secure enclaves provide local immutable storage capabilities by protecting cryptographic keys and sensitive data from tampering or unauthorized access.
Using immutable technologies and immutable storage can be implemented on conventional storage devices in the on-premises infrastructure. Optical media such as CD-R, DVD-R and Blu-Ray, as well as SD flash cards, can help to protect small amounts of data that can be convenient for individual users in the manual mode. As for organizations and production environments, a file system with WORM configuration and other solutions for scalable storage can be implemented for efficient protection with automation. Cloud-based immutable storage solutions can serve a broader range of use cases, including remote access and collaboration.
Is tape an immutable storage media?
Tape storage can be used to provide a form of immutable storage. Tape storage is a versatile medium that allows data to be written, overwritten, and deleted like other forms of storage. However, organizations can implement practices and policies to make tape storage behave in an immutable manner.
Organizations can use a write-once strategy when storing data on tape that is useful for backup to tape. This means that data is written to the tape once, and after that, the tape is treated as read-only. Once data is written to a tape in this manner, it cannot be altered or deleted without physically destroying the tape. Tape cartridges have a write-protected switch. There are also special VolSafe cartridges that can be used only once to write data.
However, it’s important to note that maintaining and managing tape-based immutable storage can be more complex and less convenient than using modern cloud-based or disk-based immutable storage solutions, which often come with built-in features for data immutability and access control.
Immutable storage on NAS
Some Network Attached Storage (NAS) systems, such as Synology NAS and QNAP NAS, support immutable storage that can be configured in the web interface of the vendor-native operating system installed on the NAS. This is one more option to configure immutable storage on-premises. Configuration of immutability for a write-once shared folder on NAS is straightforward.
Immutable Backup
An immutable backup is a backup that cannot be altered or deleted. Immutable backup is one of the most popular use cases of immutable data storage. If an expiration period is set, the immutable backup can be deleted only after this period expires. Immutable backups are used by organizations of all industries.
Backups are one of the primary targets for ransomware attackers because the attackers know that having a backup allows a victim to restore the data without paying a ransom. Backups located on immutable storage protect users and organizations against data encryption, data corruption, and deletion in backups.
When using the 3-2-1 backup rule, which requires having at least 3 copies of data on at least 2 different mediums, one of which is stored offsite, it is more reliable to have one data copy on storage with immutability. It can be an additional (fourth) data copy. If primary copies of data are compromised, it is possible to restore data from the immutable backup.
Backup to immutable storage with NAKIVO
NAKIVO Backup & Replication is a modern data protection solution supporting backing up data to repositories that support immutability. You can configure immutability by deploying a backup repository in the following locations:
- A physical or virtual machine:
- A backup repository with immutability that is assigned to a Transporter installed on a Linux machine
- A public cloud with immutability supported:
- Amazon S3
- Azure Blob Storage
- Wasabi
- Backblaze B2
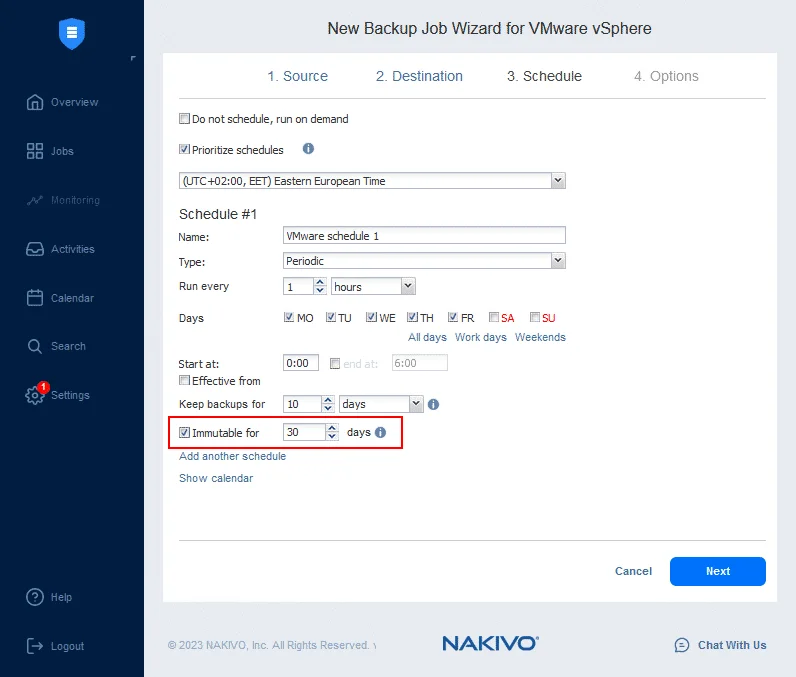
Additionally, you can deploy a virtual appliance for VMware vSphere and pre-configured Amazon Machine Image (AMI) for Amazon EC2 with a hardened built-in backup repository with immutability enabled.