How to Configure a vSphere SSO Domain in vCenter
A key part of vSphere infrastructure administration is being able to assign roles and permissions for vSphere resources. Managing logins and privileges in a VMware vSphere vCenter Server environment is critical for several reasons. You want to allow granular permissions and also provide an audit trail of the actions performed in the vCenter environment.
Let’s take a look at key points, including assigning roles or permissions based on vCenter Single Sign-On and Active Directory for vCenter SSO configuration.
What Is vCenter SSO Domain?
VMware vCenter Single Sign-On (SSO) is an authentication component of VMware vSphere for identity management. SSO authenticates a user to access different vSphere components using the credentials of a single account. SSO relies on a secure token mechanism to allow multiple vSphere components to communicate with each other.
The suite of VMware vSphere products integrates with vCenter through the SSO authentication mechanism. This allows you to use SSO to control or grant permissions to resources across the suite. Note that SSO doesn’t replace the VMware Horizon Identity Manager. Find out more in our VMware Horizon and VDI post.
Starting with vSphere 5.1, VMware introduced SSO to streamline the management of multiple ESXi hosts and other vSphere resources and improve the security of the vSphere authentication mechanism with the same user credentials. SSO allows not only Active Directory authentication, but also any other authentication source based on Security Assertion Markup Language (SAML) 2.0.
Note that a vCenter SSO identity source can be associated with a domain but it is not a replacement for Active Directory. SSO can interact with Active Directory and federate authentication and related queries to an Active Directory domain controller. You do not need to configure an Active Directory domain to use vCenter SSO if you don’t have an AD domain controller in your environment – SSO has an internal user store for authentication purposes.
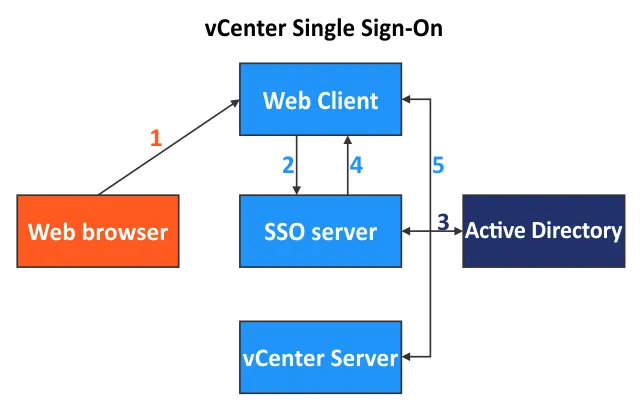
How vCenter SSO works
- A user logs in to VMware vSphere Web Client.
- The SSO server receives the username and password entered by the user.
- The request is forwarded by the SSO server to the appropriate authentication mechanism, such as Active Directory or local authentication.
- After successful authentication, SSO passes the token to VMware vSphere Client.
- The token can be used for authentication directly with vCenter Server and other VMware vSphere components.
The services used for vCenter Single Sign-On are:
- User authentication
- Security token service
- Authentication through certificates
- SSL for secure traffic
User authentication is performed through a vCenter built-in identity provider or an external identity provider (IdP). The built-in provider supports Active Directory, OpenLDAP, local accounts, integrated Windows authentication, smart card, Windows session authentication, and RSA securID. A security token service issues SAM tokens that represent the user’s identity.
vCenter SSO Configuration
The SSO piece of the vCenter infrastructure is handled by the Platform Services Controller when vCenter is installed. The Platform Services Controller is set up during the configuration of the vCenter Server Appliance (VCSA), which is provided as an almost pre-configured VM template deployed in vSphere. The VCSA runs on the Linux-based Photon OS. The Platform Services Controller also runs certificate services, licensing services, authentication framework, and appliance management.
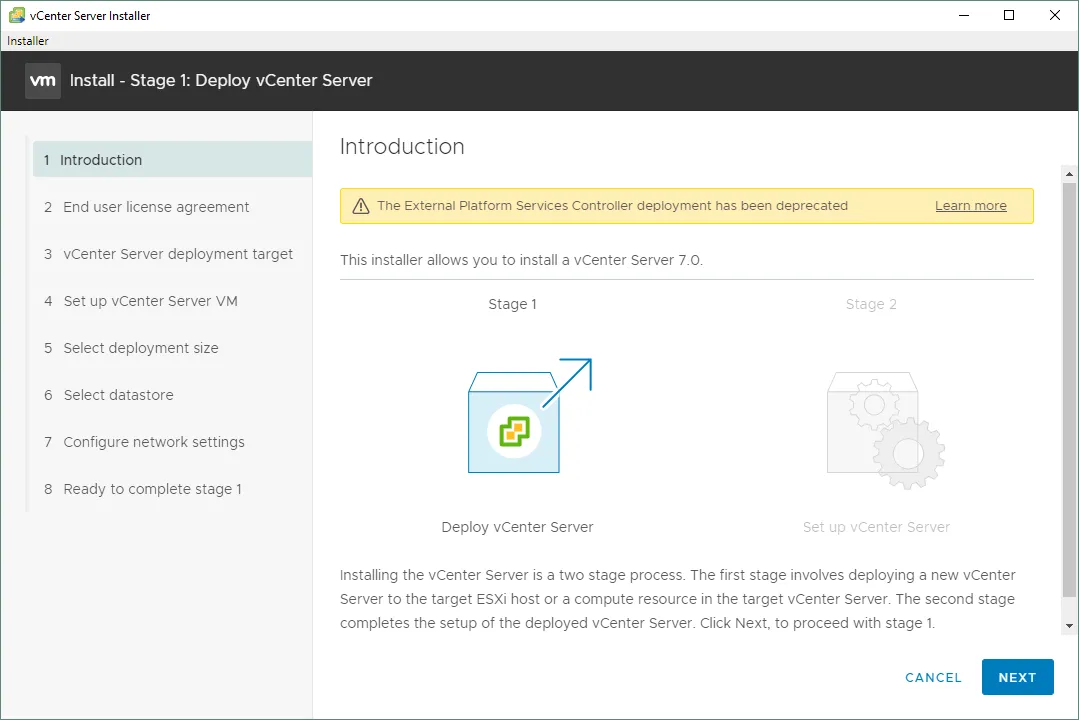
In vCenter versions v.6.7 and older, the PSC could be configured as the Embedded Platform Services Controller or an External Platform Services Controller. In vSphere v6.7, the External Platform Services Controller was deprecated. In vSphere 7, you can install vCenter using only the Embedded Platform Services Controller.
In the screenshot below, you can see the step 1 (Introduction) of Stage 1 when installing vCenter 7 and a warning message that you can no longer use the External Platform Services Controller.
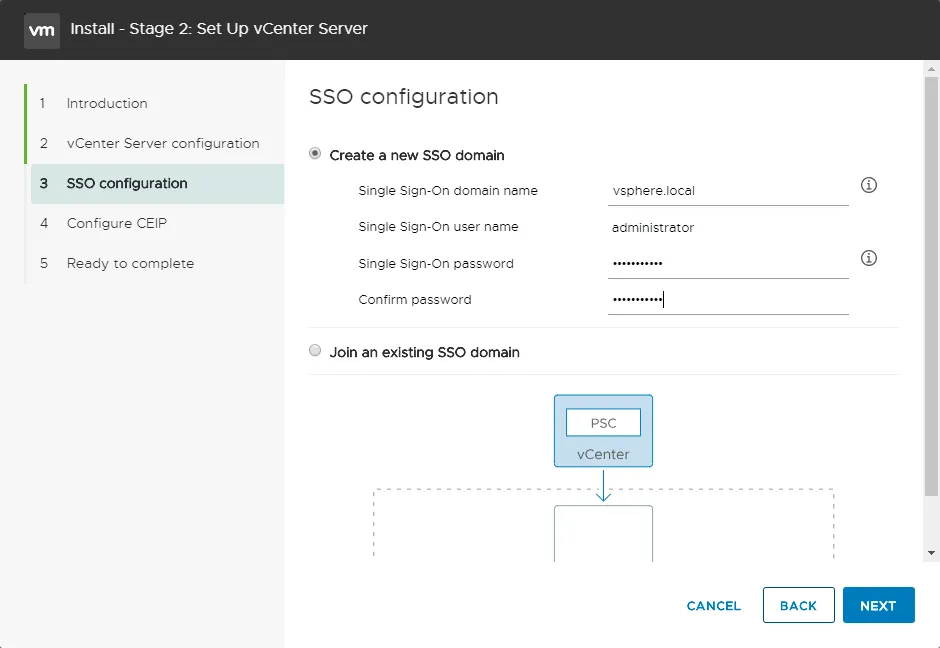
An SSO domain for vSphere is configured during the deployment of the vCenter Server appliance. You can see more details for vCenter SSO configuration at step 3 of Stage 2 when deploying vCenter (see the screenshot below). The SSO administrator, password, SSO domain name, and SSO Site name are configured during installation.
You can create a new SSO domain or join an existing SSO domain. The vCenter SSO domain that you create during the first vCenter installation is the default identity source in your VMware vSphere virtual environment.
The SSO domain is the default identity source of the vSphere environment when no other authentication domain (such as Active Directory) is specified. As already mentioned, SSO provides a token exchange mechanism (based on SAML) for authenticating with identity sources such as Active Directory, etc. You should also keep in mind that issues can arise if you set the SSO domain to mirror the AD domain name. Many choose an SSO domain name with “.local” as a suffix.
vCenter SSO domain name: best practices
The vCenter SSO domain name best practices involve using the vsphere.local domain name in small environments, but it can also be used in large environments. The vsphere.local SSO domain name fits well for interoperability in VMware vSphere, including the components such as vRealize Automation. If you are not sure what vCenter SSO domain name to use, use vsphere.local.
The SSO domain name used for local authentication in vCenter must not be the same as the name of the existing Active Directory domain. Use Active Directory integration to use the AD domain and its name if needed after installing vCenter. Enter a vCenter SSO domain name using lowercase characters.
Post-installation vCenter SSO configuration
You can edit the vCenter SSO configuration after you deploy VMware vCenter Server.
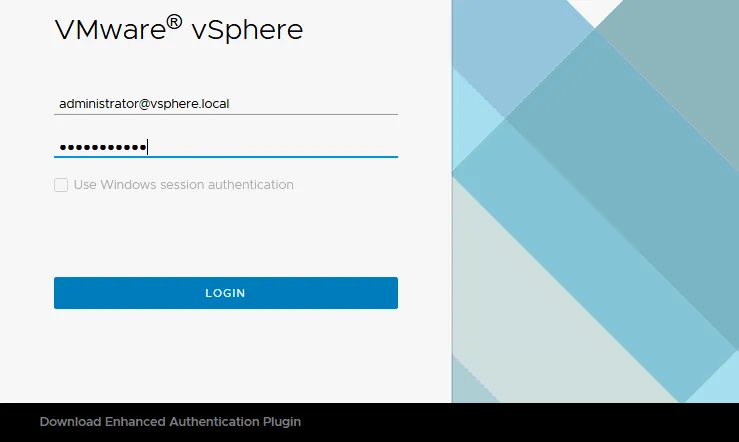
Log in to the web interface of VMware vSphere Client by using your existing administrator account to manage vCenter, for example, administrator@vsphere.local.
Note: If to manage vCenter you are using a browser to access VMware vSphere Client from a Windows machine that is a member of an Active Directory domain (after being logged in Windows as a domain user), and this domain is configured as a vCenter SSO domain, you can select Use Windows session authentication for more convenience. If this checkbox is grayed out (inactive), you need to download the Enhanced Authentication Plugin. Below we explain vCenter SSO configuration using an existing Active Directory domain.
Adding an Active Directory domain
We can configure the integration of vCenter authentication with Active Directory and use the Active Directory domain as a vCenter SSO domain. We assume that you already have an Active Directory domain controller configured and won’t go into the details of the AD configuration process in Windows Server. Remember that you should create regular Active Directory backups, especially if many services use AD for authentication.
Perform the following actions to edit vCenter SSO configuration and integrate with Active Directory:
- Click the menu icon in the top left corner of the web interface. Scroll to the Single Sign On section in the left pane and click Configuration.
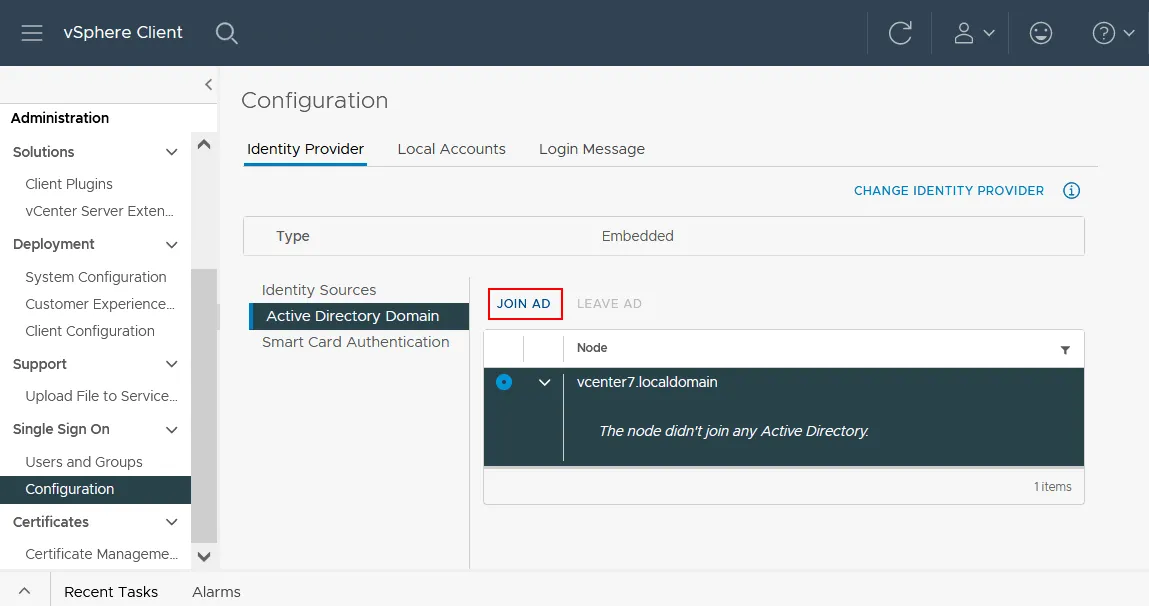
- Select the Identity Provider tab and then select Active Directory Domain.
- Click Join AD to join the Active Directory domain to be used for vCenter Single Sign-On (as a vCenter SSO domain).
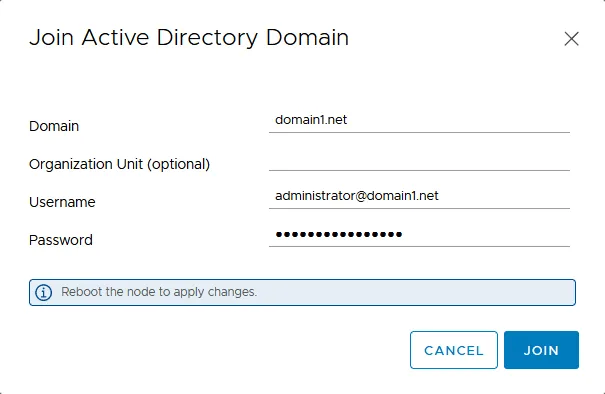
- Enter a domain name, select an organization unit (optional), and enter AD domain administrator credentials (username and password).
- Click Join and reboot the vCenter instance (VCSA) to apply the changes.
Identity provider
You can use an alternative identity source for your vCenter Single Sign On domain.
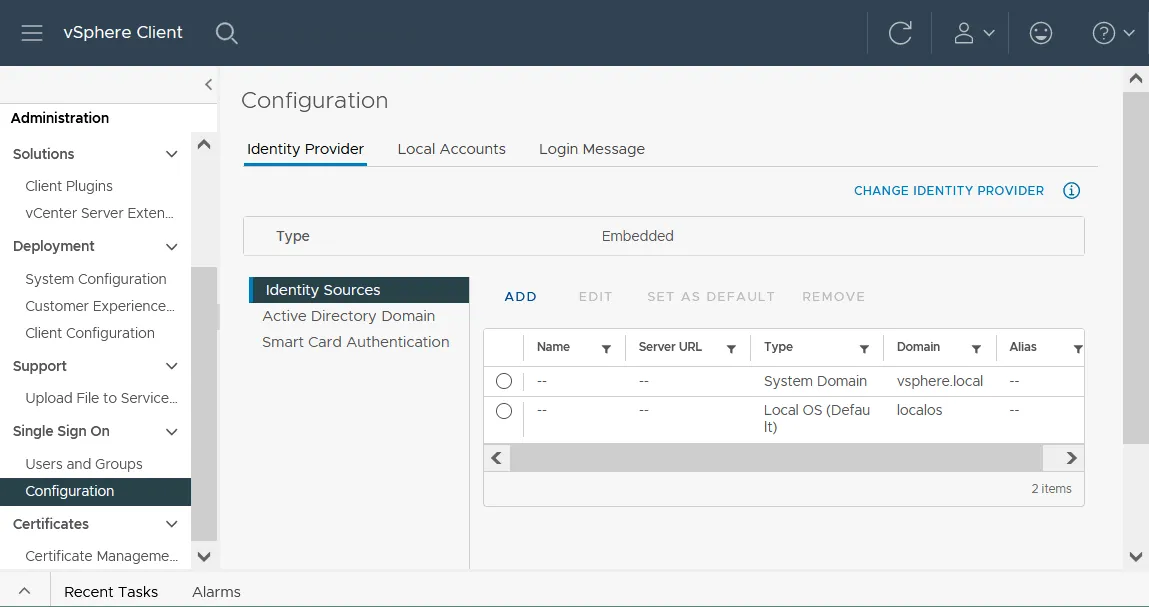
- Go to Administration > Single Sign On > Configuration in VMware vSphere Client and click Identity Sources in the Identity Provider tab.
- Select the available identity source or click Add to add a new one.
You can select the Local accounts tab and configure the password expiration time and other password policies.
Managing users and groups
Once you have configured a vCenter SSO domain, you can create users and add the users to groups in order to provide the appropriate permissions.
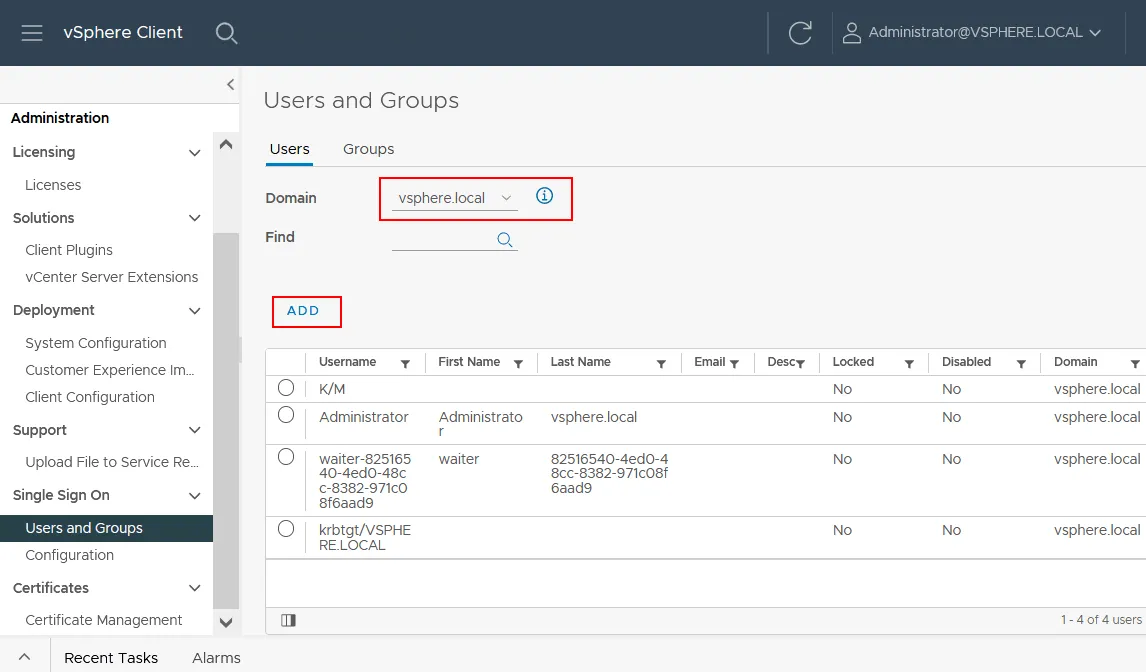
- Click Users and Groups under the Single Sign On section in the left pane of the vCenter administration page.
- Select the Users tab.
- Select a domain that can be a default (built-in) vsphere.local domain or an Active Directory domain that you added manually to be used as a vCenter Single Sign on domain.
- Click Add to add a new user for the selected domain.
- Fill out the required fields and save the settings.
The advantages of group management are the ability to assign the needed permissions to a group and add multiple users to the group in order to grant them the permissions automatically.
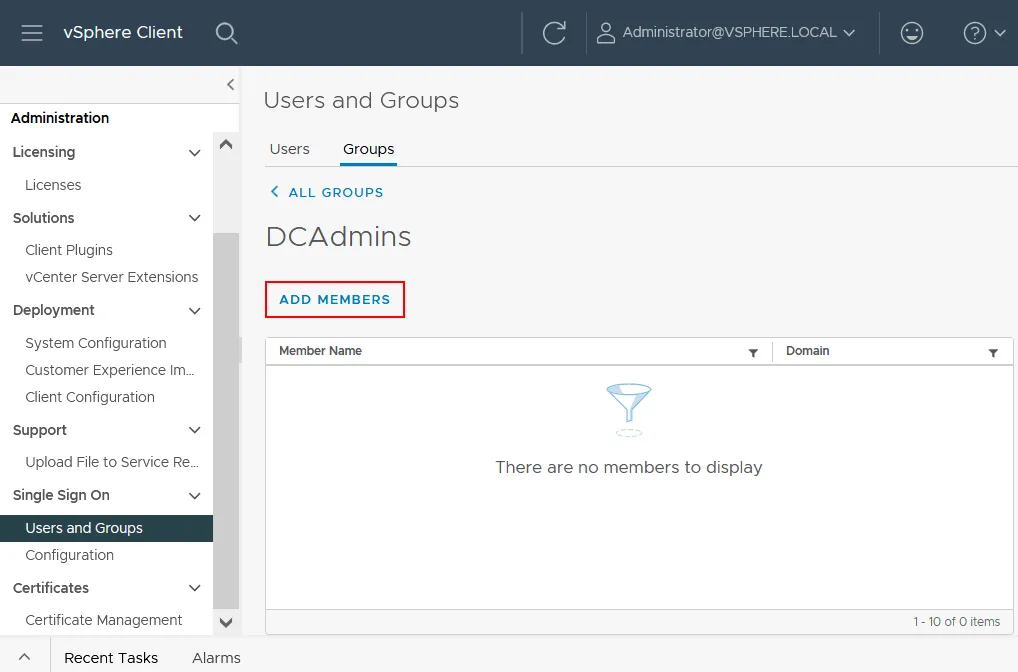
- Select the Groups tab on the Users and Groups page.
- Click Add members.
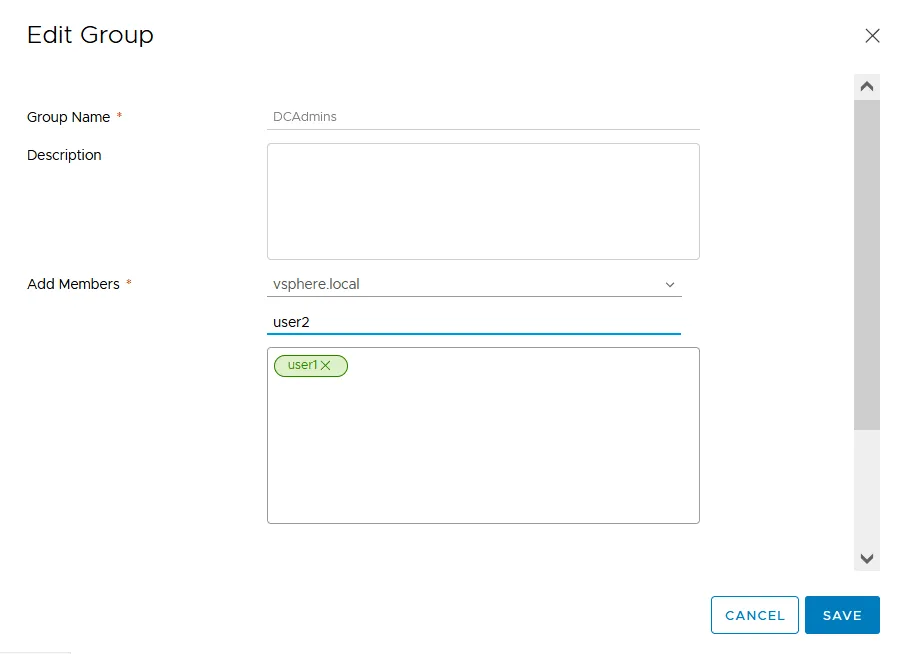
- Fill out the required fields, such as group name, and select from which domain to add members. It can be a built-in vCenter SSO domain such as vsphere.local or an Active Directory domain.
- Add the members (users or groups) from the selected domains and click Save.
Don’t delete predefined users and groups (the ones that exist after vCenter clean installation).
Wrapping Up
It is recommended that you backup your vCenter Server Appliance VMs and machines running Active Directory domain controllers. These machines are used for centralized management and authentication, and any failure can lead to severe repercussions and downtime.